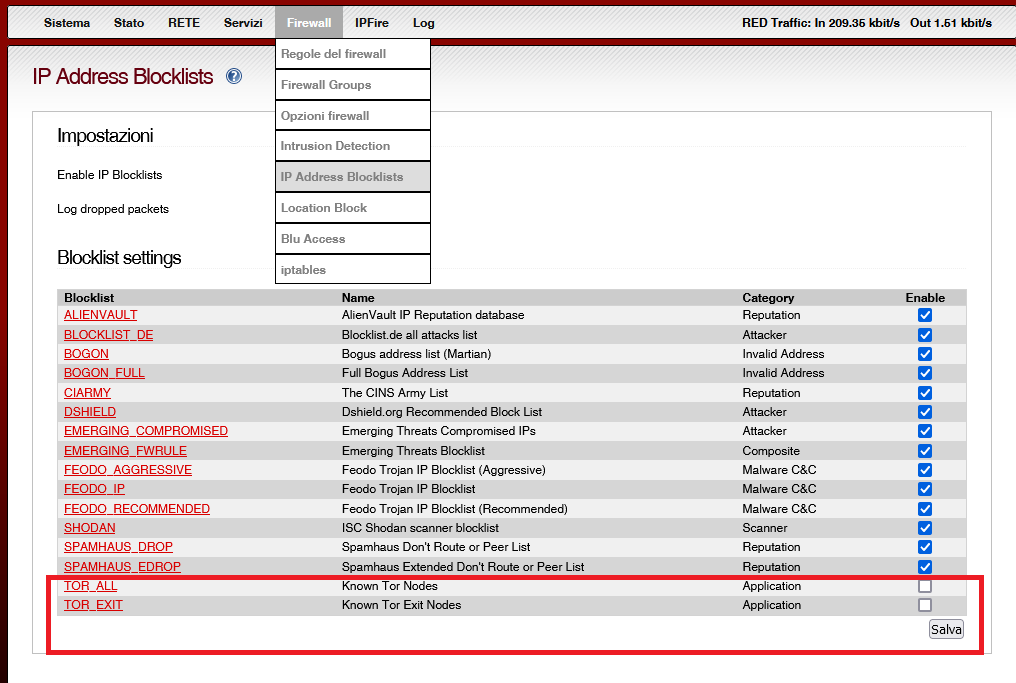
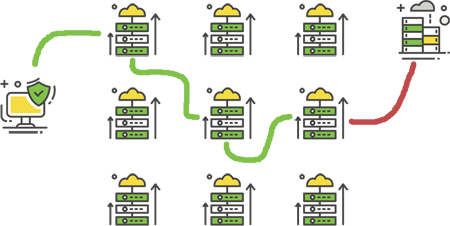
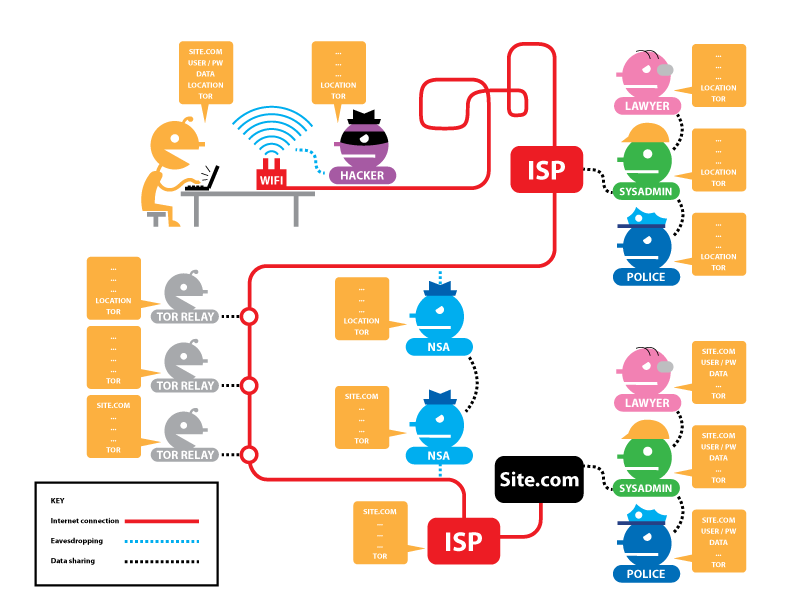
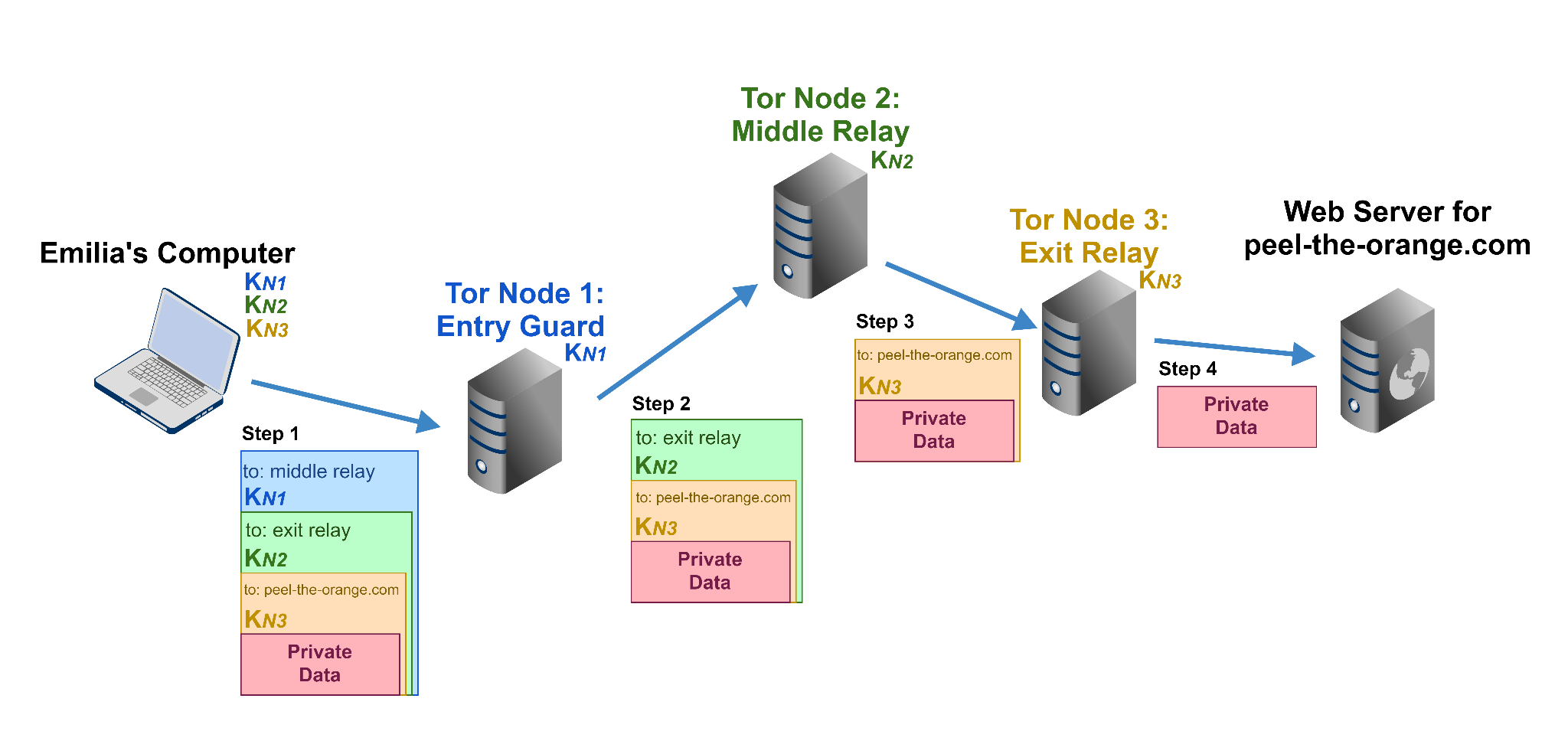
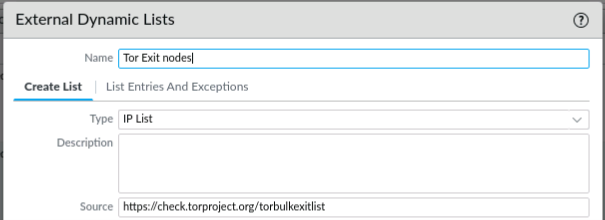
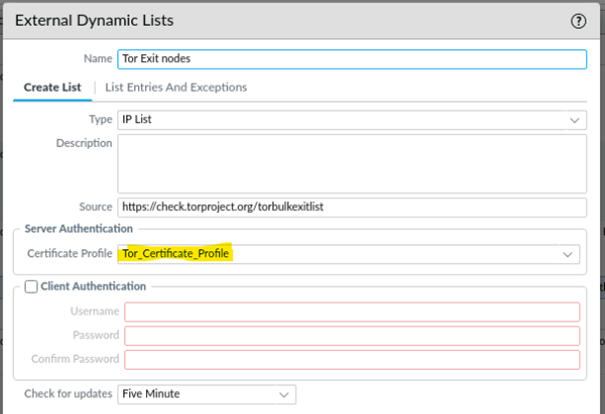
The components of the Tor network. After downloading the node list from... | Download Scientific Diagram
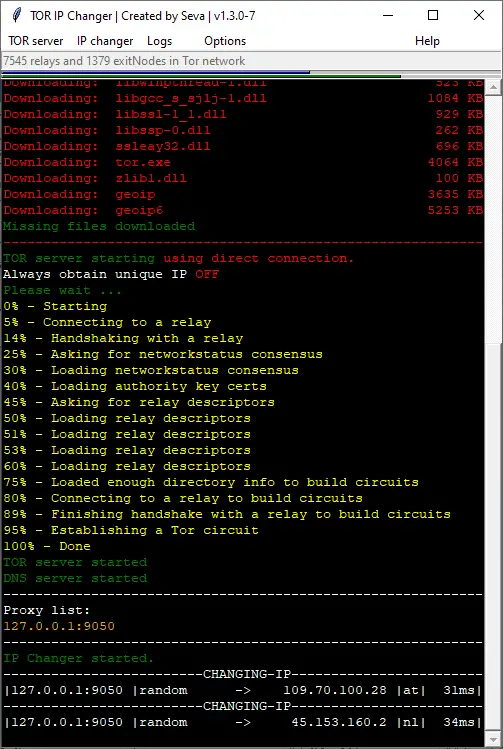
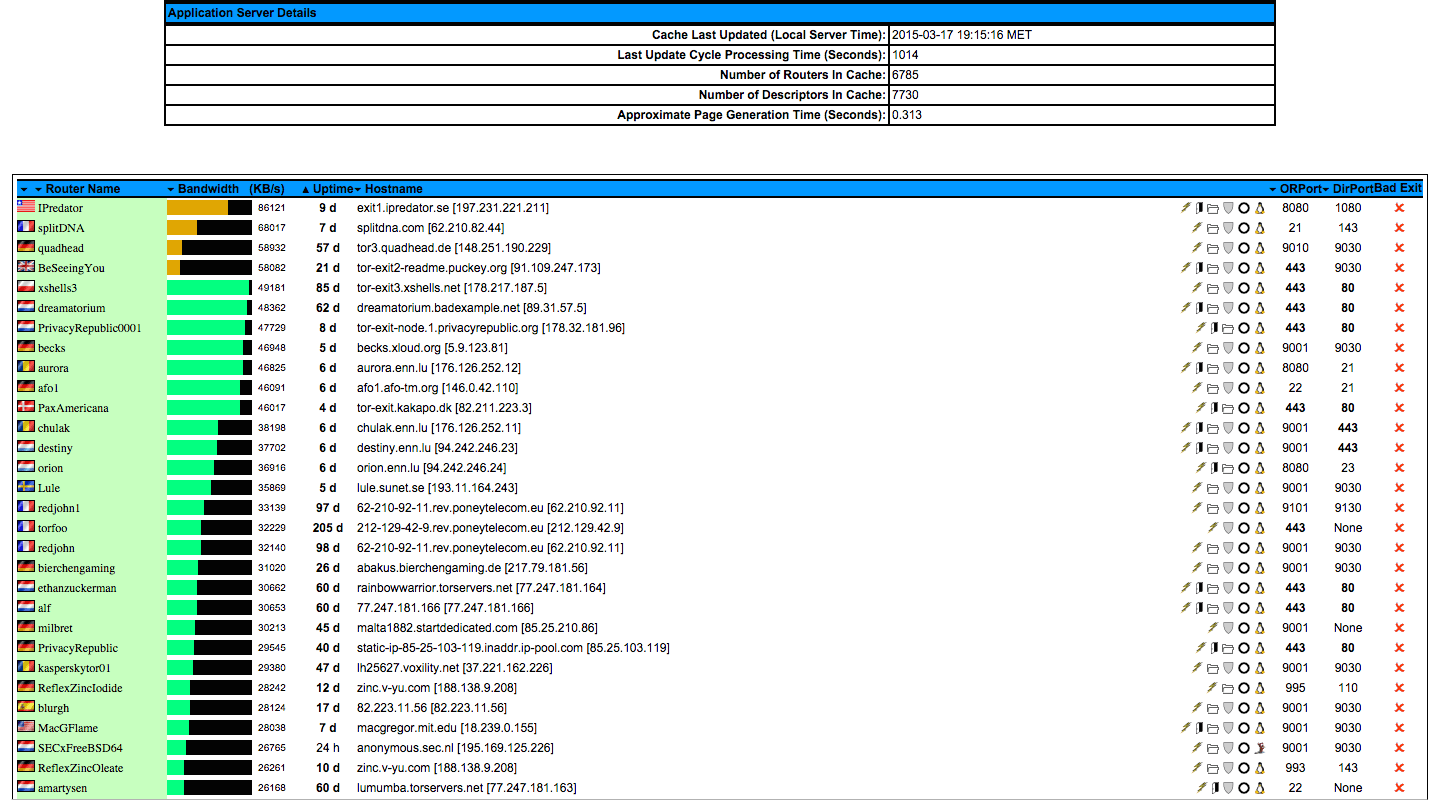
Tor ip changer - request new identity every Seconds - Penetration Testing Tools, ML and Linux Tutorials
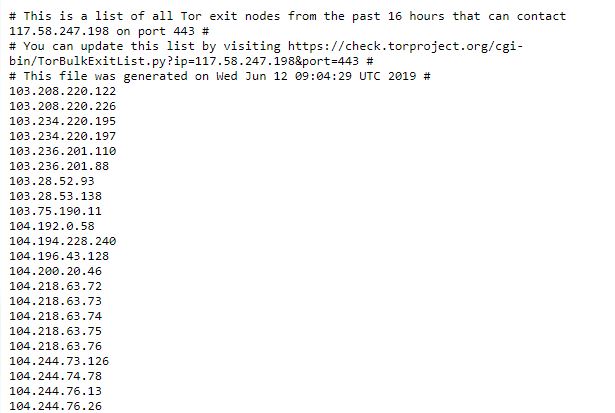
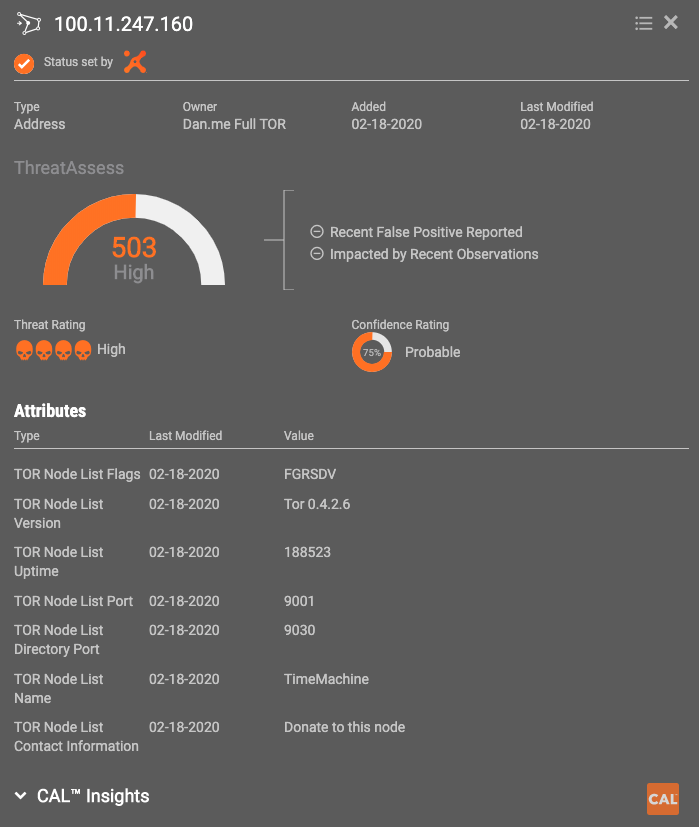
GitHub - SecOps-Institute/Tor-IP-Addresses: Hourly checked and updated list of IP Addresses of Tor and Tor Exit Nodes